Demystifying the Code - Know your CCoP!
Written by:
Principal Consultant
Sapience Consulting

Since the enactment of the CyberSecurity Act in 2018, CSA has released and subsequently updated the CyberSecuruity Code of Practice (CCoP). This Code is intended to specify the minimum requirements that the Critical Information Infrastructure Organization (CIIO) shall implement to ensure the cybersecurity of its CII and CIIOs are expected to implement measures beyond those stipulated in this Code to further strengthen the cybersecurity of the CII based on the cybersecurity risk profile of the CII.
The varying levels of Cybersecurity across the 11 CII sectors have also not made it easy for the regulator to establish common ground for all the sectors and yet ensuring a minimum level of protection required to meet growing threats against CIIOs.
Version 1 of the CCoP was initially released in September 2018 and updated in December 2019. Version 2 was release in July 2022 and Revision 1 to CCoP subsequently released in December 2022.

With the release of CCoP version 2, CSA is looking at ensuring that CIIOs level up their cybersecurity competencies and capabilities to better meet the challenges of the evolving Cyber Threat Landscape where threat actors today have demonstrated successfully their abilities to make use of a variety of sophisticated tactics, techniques and procedures (TTPs) to target, compromise and exploit CII sectors.
CCoP version 2 incorporated the Singhealth COI recommendations and also integrated the version 1’s Annex A which focused on security controls specific to Operational Technology (OT) environments. The approach taken with version 2 was one taken to ensure that CIIOs are able to improve the odds of defending against attackers and their utilization of increasing complex TTPs while ensuring open lines of communication between the government and the private sector to allow for a coordinated approach to any identified cyber attacks and allow for timely identification, discovery and response.

The design principles that guided CCoP version 2 was adopted based on a threat based approach to allow CIIOs to focus on areas which matter most to their environment and allocate resources in the most effective manner.
Another guiding principle was the acknowledgement that all the 11 CII sectors have varying levels of cyber maturity and threat exposure and a cookie cutter approach will not be an effective way of building a cyber posture to support the CIIO. Hence controls should be tailored to specific environments to allow for adequate defences against sector specific threats affecting the digital terrain.
The third principle involves proactive defence. CIIOs are required to be acutely aware of what is happening within their threat environment and put in place adequate threat intelligence capabilities to allow CIIOs to know what is happening within the cyber threat landscape and put in place organizational practices to detect, defend and recover from any potential cyber attacks
A holistic coverage to ensure that the CIIO’s risk and threat posture is secured drives the fourth principle where emphasis is placed to ensure that within the CIIO organization, there exist a comprehensive Governance, Risk and Compliance (GRC) structure to facilitate the effective implementation of the three lines of defence; Operatons, Risk and Compliance.
The last design principle looks at how CIIOs are now expected to be outcome based in terms of looking at securing their CII environment instead of focusing on individual specific controls and how these controls needs to be implemented. This is a important design principle as no two organisations are the same and no two environments are similar. What works for one organization may be grossly ineffective for another.
CCoP 2.0 amalgamates new practices drawn from the SingHealth COI, National Institute of Standards and Technology (NIST) and Public Sector Data Security Review Committee (PSDSRC) into the practices specified within CCoP 1.0. Certain CCoP 1.0 clauses were also enhanced and revised for clarity and to ensure non ambiguity in understanding
A new addition to the CCoP 2.0 would be Domain Specific practices which are targeted at CIIOs with a set of specific cyber requirements. While the current edition of the CCoP 2.0 currently only contains a set of practices targeting Domain Name System Security Extension (DNSSEC), it would be expected that with the evolving digital threat landscape, new practices will be added into this section over time.
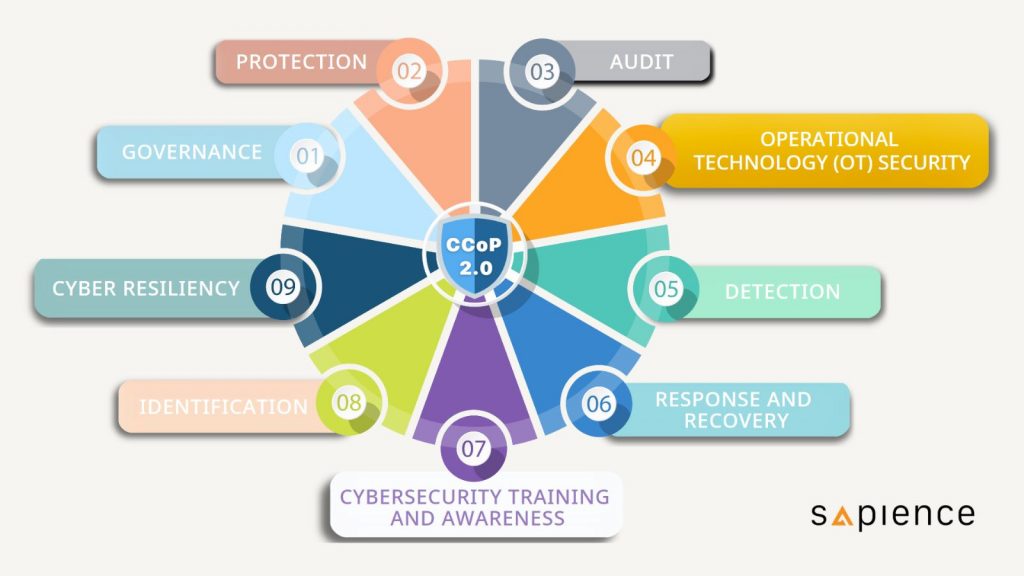
The structure of the CCoP has also been revised with the introduction of CCoP 2.0 with controls now being grouped into protection categories. These categories are designed with the intention of providing clarity in terms of the controls CIIOs are required to implement and maintain.
The categories are grouped as follows
• Audit
• Governance
• Identification
• Protection
• Detection
• Response and Recovery
• Cyber Resiliency
• Cybersecurity Training and Awareness
• Operational Technology (OT) Security
And comprises of over 200 auditable compliance clauses which represents a almost 100% increase over the number of compliance clauses specified within CCoP 1.0
From a regulatory compliance perspectives, a number of dates now become significant for CIIOs. For existing CIIOs with CIIs already designated by CSA, compliance to CCoP 2.0 will be mandatory from 4th July 2023 onwards. This is effectively 12 months from the effective date of the official release of CCoP 2.0.
For newly designated CIIs, CIIOs will have 12 months from the designated date to ensure compliance with the code.
CII Designations are valid for 5 years upon initial designation by CSA and with the initial designations done after the enactment of the Cybersecurity Act in 2018, most of the currently designated CIIs will require re-designation in 2023. For these CIIs, compliance to the code will be required upon the effective date of the re-designation.
The CyberSecurity Code of Practice will be a work in progress and rightly so, to ensure that it remains relevant to meet the threats posed within today’s constantly evolving digital landscape. While the cyber best practices codified within the CCoP may be a compliance requirements for CIIOs, private organizations should adopt these practices where feasible to ensure that the organization’s security posture is adequately addressed.
This article is the first of a series of articles on the Cyber landscape in Singapore and the opinions expressed within this article is not representative of CSA’s position nor should it be used as a interpretation for compliance to the Cybersecurity Act or the Cybersecurity Code of Practice. If there are topics of interest which you would like to read about, do drop us a mail at [email protected]. In the meantime, do look out for our next article where we will look at the protection categories in detail
Learn more about Cybersecurity with these available courses today!