Security by Design and Threat Modelling as part of Risk Management :
Wishful Thinking or Work in Progress?
Written by:
Principal Consultant
Sapience Consulting

Integrating security by design and threat modeling into an organisation’s risk management process is essential for proactively addressing security vulnerabilities and enhancing overall resilience. Here’s a detailed approach to effectively accomplish this integration:
Understanding Security by Design and Threat Modeling
🛡️ Security by Design
Security by design emphasises incorporating security considerations into the initial phases of system development and architecture. It involves creating systems that are secure from the ground up, rather than adding security measures as an afterthought.
🔍 Threat Modeling
Threat modeling is a structured approach for identifying and evaluating potential security threats to an application or system. It helps organisations understand potential attack vectors and vulnerabilities, allowing them to mitigate risks effectively.
The 7-Step Integration Framework
Establish a Security Framework
Define Security Policies: Develop clear security policies that align with the organization’s risk management framework. This includes outlining roles and responsibilities for security practices.
Adopt Standards: Consider adopting recognized standards, such as ISO 27001 or NIST, to guide the implementation of security measures.
Incorporate Security into Development Life Cycle (SDLC)
Integrate Early: Ensure that security practices are integrated into every phase of the SDLC, from planning and design to development, testing, and deployment.
Security Reviews: Conduct regular security reviews during development to identify potential security weaknesses.
Conduct Thread Modelling
Identify Assets: Begin by identifying critical assets that need protection, such as sensitive data and applications.
Identify Threats: Use methodologies like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) to identify potential threats.
Analyse Vulnerabilities: Assess potential vulnerabilities related to each identified threat and prioritise them based on risk.
Risk Assessment
Integrate Findings: Incorporate the results of the threat modeling process into the overall risk assessment framework. This involves evaluating the likelihood and impact of identified threats on assets.
Prioritise Risks: Use the information from threat modeling to prioritise risks, allowing for targeted resource allocation for mitigation.
Mitigation Strategies
Develop Mitigation Plans: For each identified threat, create a plan that outlines the necessary controls or measures to mitigate the risk. This may include technical controls (e.g., encryption, access controls) and procedural controls (e.g., incident response plans).
Implement Controls: Ensure that the controls identified in the mitigation plans are implemented effectively within the system.
Continuous Monitoring & Review
Monitor Security Posture: Continuously monitor the effectiveness of security controls and threat landscape changes. This can be achieved through security audits, vulnerability assessments, and penetration testing.
Iterative Improvement: Treat security by design and threat modeling as iterative processes. Regularly revisit threat models and risk assessments as systems evolve and new threats emerge.
Training & Awareness
Educate Staff: Provide training for development teams on security best practices and threat modeling techniques. This ensures that everyone is aware of the importance of integrating security into their work.
Promote a Security Culture: Foster a culture of security within the organisation where employees understand the importance of security considerations in their roles.
Focus on Threat Modeling: STRIDE
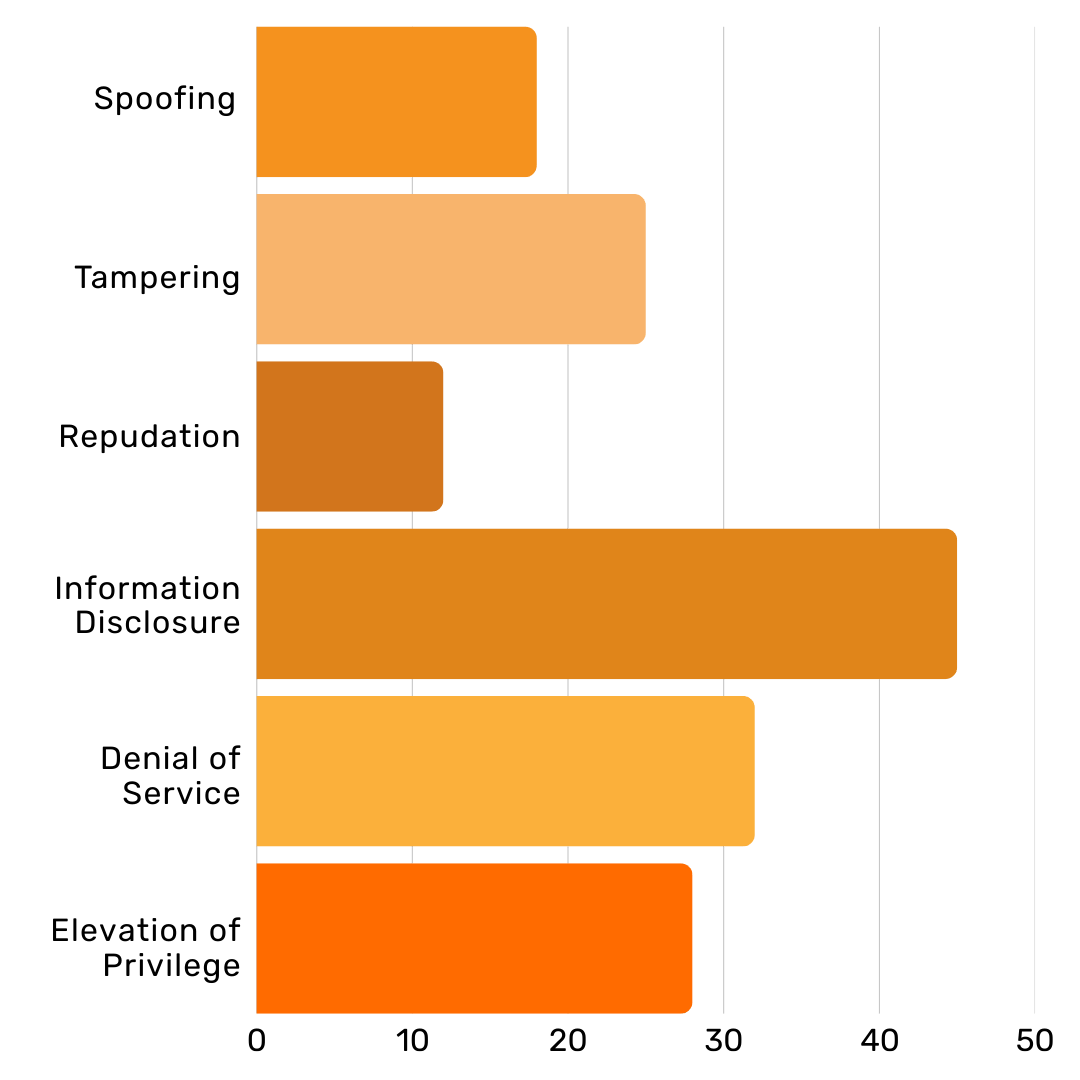
The STRIDE model is a common framework for identifying and categorising threats. Prioritising these categories helps focus mitigation efforts on the most likely or impactful attack vectors. This chart shows a hypothetical distribution of identified threats in a typical web application.
SDLC: Security at Every Stage

Integrating security is not a one-time check. It's a continuous practice woven into the fabric of development. Each phase presents a unique opportunity to strengthen defenses, reducing costs and risks associated with fixing vulnerabilities post-release.
Tools and Resources
Leveraging the right tools automates and streamlines the integration of security. These categories represent a foundational toolkit for any organisation aiming to mature its Security by Design practices.
Threat Modeling Tools
Utilise tools like Microsoft Threat Modeling Tool, OWASP Threat Dragon, or IriusRisk to facilitate the threat modeling process.
Risk Management Frameworks
Implement frameworks like FAIR (Factor Analysis of Information Risk) to enhance risk assessment processes.
Continuous Integration/
Continuous Deployment (CI/CD) Security Tools
Leverage automated security tools in CI/CD pipelines to identify vulnerabilities during the development process.
Conclusion
Ultimately, the journey from wishful thinking to a proactive security posture is a matter of culture. It requires moving beyond a simple checklist and embedding security as a fundamental part of every role—from the developer to the project manager. By embracing security by design and leveraging threat modeling as a core practice, organisations don’t just reduce risk; they build a more resilient, innovative, and trustworthy foundation for future growth. The question isn’t whether you can afford to do this, but whether you can afford not to.
As a trusted leader in professional development, Sapience empowers you to invest in your future.
Don’t wait – Explore our available funding and leverage our expertise to upskill without financial strain.










