Fortifying Your Future:
How ISO/IEC 27001 Builds Secure, Agile, and Trusted Businesses
Written by:
Principal Consultant
Sapience Consulting
In an era where digital transformation is relentless and data is the new currency, the spectre of cyber threats looms larger than ever. From sophisticated ransomware attacks to insidious data breaches, organisations globally are grappling with a complex and evolving risk landscape. In this environment, establishing and maintaining information security is not just an IT concern; it’s a fundamental business imperative. For businesses aiming to thrive, the international standard ISO/IEC 27001 and its supporting family of standards offer a robust and globally recognised framework to achieve precisely that: becoming secure, agile, and, crucially, trusted.
But what does it truly mean to leverage these standards effectively? It’s more than a certificate on the wall; it’s about ingraining a security-first mindset into the very fabric of an organisation.
Navigating the Modern Threat Landscape
In an era of relentless digital transformation, the volume and sophistication of cyber threats are escalating. Organisations must adopt a proactive and structured approach to information security to protect their most valuable assets.
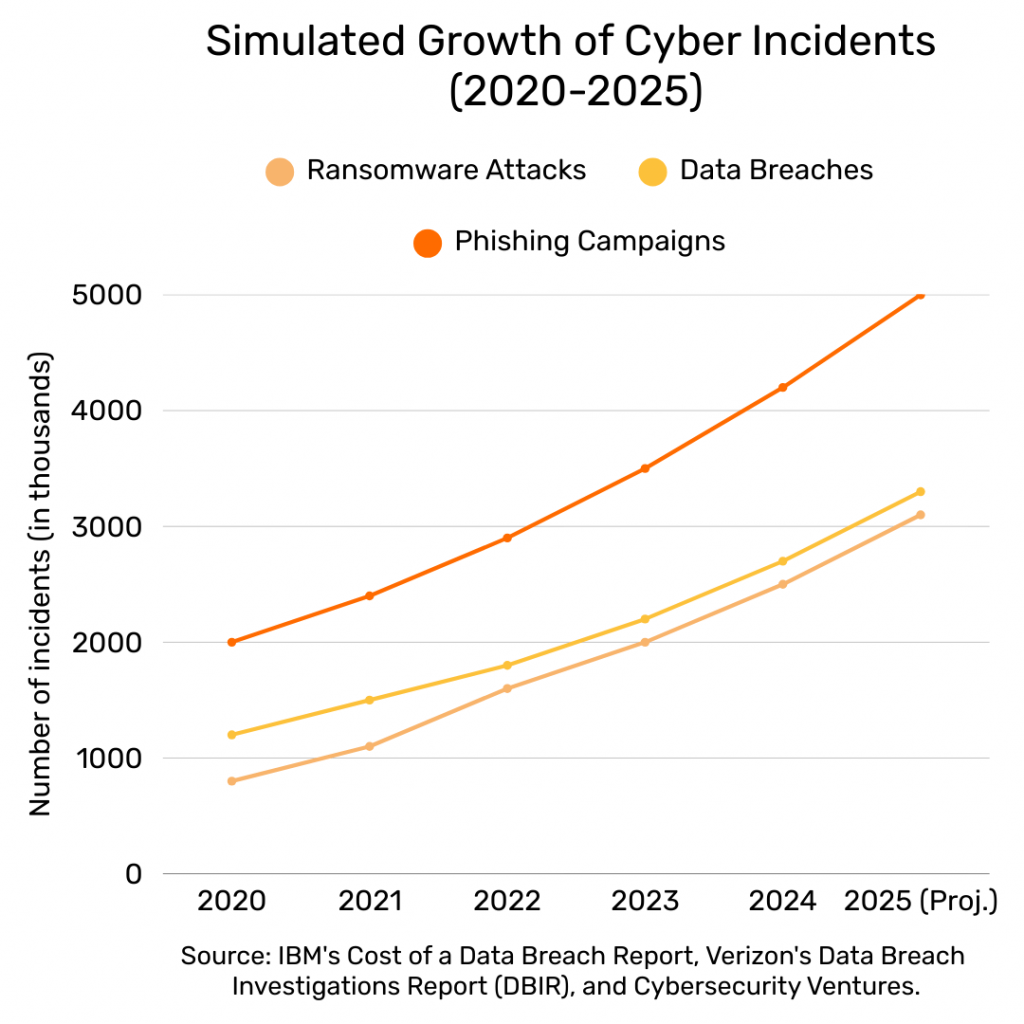
This chart (Fig. 1) illustrates a significant projected rise in various cyber threats. ISO/IEC 27001 provides a framework to mitigate these risks effectively by building a resilient security posture.
The Power of ISO/IEC 27001:
The Triad of Security, Agility, and Trust
ISO/IEC 27001 provides the blueprint for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). An ISMS is a systematic approach to managing sensitive company information so that it remains secure. It encompasses people, processes, and IT systems by applying a risk management process.

This could involve anything from robust access control mechanisms and encryption protocols to employee security awareness training and incident response plans. The result is a significantly hardened security posture, reducing the likelihood and impact of security incidents.

This secure foundation gives organisations the confidence to innovate, knowing their valuable information assets are protected. For instance, as businesses increasingly adopt cloud services, standards like ISO/IEC 27017 (code of practice for information security controls for cloud services) provide tailored guidance within the ISO/IEC 27001 framework, enabling agile and secure cloud adoption.

In many industries, ISO/IEC 27001 certification is becoming a prerequisite for doing business, opening up new market opportunities and providing a distinct competitive advantage. It signals that an organisation is a responsible custodian of information.
Beyond the Checklist :
Applying ISO/IEC 27001 to Real Business Challenges
The true power of ISO/IEC 27001 is realised when it moves beyond a mere compliance exercise and is strategically applied to address tangible business challenges. Organisations must understand how to interpret and implement its requirements in the context of their unique operational realities.
Top Drivers for ISO 27001 Adoption
Addressing Real Business Challenges
ISO/IEC 27001 is not a theoretical exercise; it provides a practical framework for solving tangible business problems. Its risk-based approach helps prioritise efforts where they are needed most, from regulatory compliance to supply chain security.
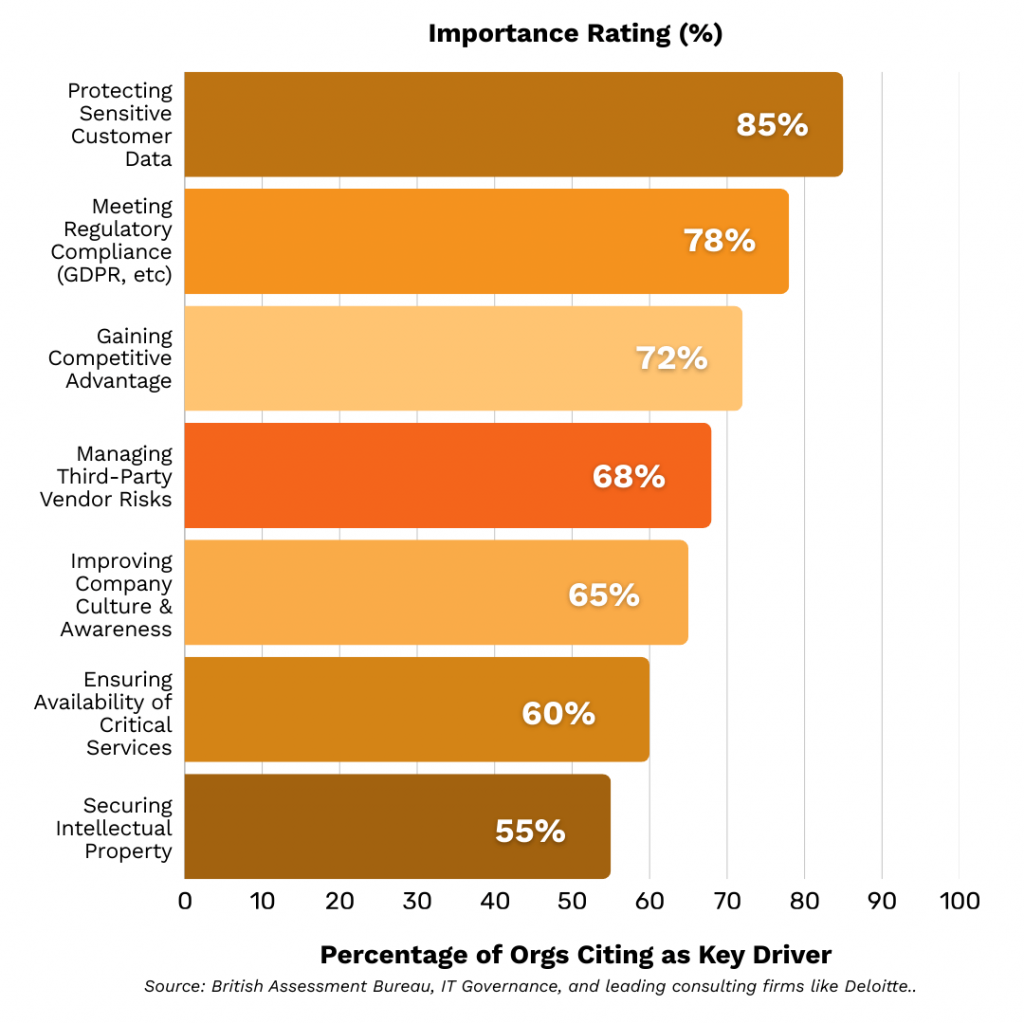
Organisations adopt ISO 27001 for a variety of strategic reasons. As shown in Fig. 2, protecting customer data and meeting regulatory requirements are primary drivers, highlighting the standard’s critical role in today’s data-driven economy.
Consider these common scenarios:
Protecting Sensitive
Customer Data
With stringent data privacy regulations like the EU’s General Data Protection Regulation (GDPR), California’s Consumer Privacy Act (CCPA), and Singapore’s Personal Data Protection Act (PDPA), mishandling personal information can lead to severe financial penalties and reputational damage. ISO/IEC 27001, particularly when augmented with ISO/IEC 27701 (which extends ISO/IEC 27001 for privacy information management), provides a framework for implementing technical and organisational measures to protect personal data, manage consent, and handle data subject requests effectively.
Securing Intellectual Property (IP)
For many businesses, IP is their most valuable asset. ISO/IEC 27001 helps implement controls to protect trade secrets, patents, and proprietary information from theft or unauthorised disclosure, whether from external attackers or insider threats.
Managing Third-Party Vendor Risks
Businesses rarely operate in isolation. Supply chains and vendor ecosystems introduce new security risks. ISO/IEC 27001 promotes processes for assessing and managing the security practices of third-party vendors, ensuring they meet the organisation’s security standards before being granted access to sensitive information.
Ensuring Availability
of Critical Services
Businesses rarely operate in isolation. Supply chains and vendor ecosystems introduce new security risks. ISO/IEC 27001 promotes processes for assessing and managing the security practices of third-party vendors, ensuring they meet the organisation’s security standards before being granted access to sensitive information.
Facilitating Secure Remote Work
The shift towards remote and hybrid work models has expanded the attack surface. ISO/IEC 27001 provides guidance on securing remote access, protecting data on endpoint devices, and ensuring that security policies are effectively applied regardless of employee location.
Supporting standards within the ISO/IEC 27000 family provide specialised guidance. For example, ISO/IEC 27005 offers in-depth knowledge on information security risk management, while ISO/IEC 27018 focuses on protecting Personally Identifiable Information (PII) in public cloud environments. Understanding and utilising these related standards allows for a more tailored and effective ISMS.
Navigating the complexities of ISO/IEC 27001 implementation and ensuring all requirements are met for successful certification can be a daunting task, especially for organisations without dedicated in-house expertise. This is where specialist consultancy firms like Sapience Consulting, can provide invaluable support. Sapience offer a range of services to guide businesses through every stage of the preparation process. This typically includes conducting thorough gap analyses to identify areas needing attention, assisting with risk assessments and treatment plans, helping to develop and document the necessary ISMS policies and procedures, delivering tailored awareness training to staff, and conducting pre-certification internal audits.
By leveraging Sapience Consulting’s experience and structured methodologies, organisations can streamline their journey to ISO 27001 certification, saving time, optimising resources, and increasing their chances of a successful first-time audit, ultimately embedding a robust security posture.
The Nexus :
Where Cybersecurity Threats Meet Compliance, Risk, and Resilience
The modern threat landscape is a complex interplay of evolving cyber threats, demanding regulatory compliance, comprehensive risk management, and robust organisational resilience. ISO/IEC 27001 sits at the nexus of these critical areas.
Cybersecurity Threats
From state-sponsored Advanced Persistent Threats (APTs) and widespread ransomware campaigns to sophisticated phishing attacks and the ever-present risk of insider negligence or malice, the threats are diverse and persistent. ISO/IEC 27001’s continuous improvement cycle (Plan-Do-Check-Act or PDCA) ensures that the ISMS adapts to these emerging threats.

Compliance
ISO/IEC 27001 doesn’t exist in a vacuum. It aligns with and helps organisations meet the requirements of numerous other regulations and legal obligations. For instance, financial institutions, healthcare providers, and government agencies often have sector-specific cybersecurity mandates. Implementing ISO/IEC 27001 can provide a solid foundation for achieving compliance across multiple frameworks, streamlining efforts and reducing the burden of disparate audits.

Risk Management
The cornerstone of ISO/IEC 27001 is its risk-based approach. It requires organisations to systematically identify, analyse, evaluate, and treat information security risks. This aligns perfectly with broader enterprise risk management (ERM) frameworks, ensuring that information security risks are considered alongside other business risks, receiving appropriate attention and resources from senior management.

Resilience
While ISO 22301 is the dedicated standard for Business Continuity Management Systems, ISO/IEC 27001 significantly contributes to operational resilience. By focusing on the confidentiality, integrity, and availability of information, it helps ensure that businesses can withstand and recover quickly from security incidents, minimising operational disruption and financial loss. Its requirements for incident management and backup procedures are key to this.
Navigating the Evolving Digital Threat Landscape:
Lessons from Leading Organisations
Leading organisations understand that information security is not a one-time project but an ongoing journey of vigilance and adaptation. They leverage ISO/IEC 27001 as a dynamic tool to navigate the ever-shifting digital threat landscape. Here’s how:
Security starts at the top. These organisations have active and visible commitment from senior leadership, who champion the ISMS and allocate necessary resources. They foster a strong security-aware culture where every employee understands their role in protecting information assets.
The Plan-Do-Check-Act cycle is embedded in their operations. They regularly review the effectiveness of their ISMS, monitor for new threats and vulnerabilities, conduct internal audits and management reviews, and take corrective actions to continually enhance their security posture.
While ISO/IEC 27001 is technology-neutral, leading organisations effectively integrate advanced security technologies within their ISMS framework. This includes leveraging AI and machine learning for advanced threat detection and response, automation for security operations (SecOps) to improve efficiency, and robust identity and access management (IAM) solutions.
They don’t wait for attacks to happen. These organisations invest in threat intelligence feeds and services to stay ahead of emerging threats, understand attacker tactics, techniques, and procedures (TTPs), and proactively adjust their defenses.
Recognising that no defense is impenetrable, they build adaptive security strategies that focus on rapid detection, effective response, and swift recovery. Their ISMS is flexible enough to incorporate new controls and processes as the threat landscape evolves.
Employees are often the first line of defense. Leading organisations conduct regular, engaging security awareness training and phishing simulations to ensure staff can identify and report potential threats.
Your Strategic Investment in a Secure Future
In conclusion, ISO/IEC 27001 and its supporting standards are not merely a set of guidelines but a strategic business enabler. They provide a clear path for organisations to build robust security capabilities, enhance operational agility, and cultivate lasting trust with customers and partners.
As the digital world continues to present both unprecedented opportunities and sophisticated threats, embracing a comprehensive information security framework like ISO/IEC 27001 is no longer optional — it’s a critical investment in your organisation’s resilience, reputation, and future success. By moving beyond a checkbox mentality and embedding these principles deep within your operational DNA, your business can confidently navigate the complexities of the digital age, secure in its foundations and trusted by all who engage with it.
As a trusted leader in professional development, Sapience empowers you to invest in your future.
Don’t wait – Explore our available funding and leverage our expertise to upskill without financial strain.










