SOC2 Attestation:
Needed or Needless in the Lion City?
Written by:
Principal Consultant
Sapience Consulting

In today’s interconnected business world, trust is paramount. Companies increasingly rely on third-party service organisations for critical functions, from financial processing to data hosting. But how can you be sure these partners are handling your sensitive information responsibly and effectively? This is where System and Organization Controls (SOC) reports come into play. These independent assessments, governed by standards from the American Institute of Certified Public Accountants (AICPA), provide crucial assurance about a service organisation’s control environment.
If you’re a service organisation, understanding SOC compliance isn’t just a regulatory hurdle; it’s a strategic imperative. A favorable SOC report can build client confidence, streamline due diligence, and even offer a significant competitive advantage. This post will demystify SOC 1 and SOC 2 reports, explain their different “types,” and outline what it takes to achieve compliance.

SOC 1 vs. SOC 2:
Understanding the Core Focus
The first step in navigating SOC compliance is understanding the fundamental difference between SOC 1 and SOC 2 reports.
SOC 1: Focusing on Financial Reporting.
SOC 1 reports are specifically concerned with a service organisation’s controls that are relevant to its clients’ internal control over financial reporting (ICFR). Think of services like payroll processing, loan servicing, or data centers hosting financial applications. If your services could impact your clients’ financial statements, a SOC 1 report is likely what their auditors will be looking for, especially for Sarbanes-Oxley (SOX) compliance. The primary audience for SOC 1 reports is the management of user entities and their external financial auditors.
SOC 2: Centering on Trust and Operational Controls.
SOC 2 reports have a broader scope, addressing a service organisation’s controls related to one or more of the five Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy. These reports are vital for organisations that manage or process customer data, such as cloud computing providers, Software-as-a-Service (SaaS) companies, and data hosting services. The audience for SOC 2 reports is wider, including user entity management, information security teams, business partners, and prospective clients.
The “Type” Distinction: Point-in-Time vs. Over-a-Period Assurance
Both SOC 1 and SOC 2 reports come in two “types,” which define the level of assurance provided:

Type 1 Report:
A Snapshot of Control Design.
A Type 1 report assesses the fairness of the presentation of management’s description of the service organisation’s system and the suitability of the design of the controls as of a specific point in time. It’s like a photograph – it shows that the controls were appropriately designed on that particular day. This report provides a foundational level of assurance and can be useful for organisations new to SOC reporting or needing to quickly demonstrate control design.

Type 2 Report:
Validating Effectiveness Over Time.
A Type 2 report goes significantly further. It includes all the elements of a Type 1 report but also assesses the operating effectiveness of those controls over a specified period, typically ranging from six to twelve months. This means the auditor has tested whether the controls have been consistently applied and are functioning as intended throughout the review period. A Type 2 report offers a higher level of assurance and is generally what user entities and their auditors prefer for ongoing reliance.
Diving Deeper: SOC 1 Requirements
For a SOC 1 report, management defines specific control objectives relevant to their clients’ ICFR.
SOC 1 Type 1 Key Requirements:
Management’s Description of the System:
A comprehensive written description of the services provided, the “as of” date, the control objectives, and the controls in place to achieve them.Suitability of Control Design:
An assessment that the controls, as described, are suitably designed to achieve the stated control objectives as of the report date.Management’s Assertion:
A formal written statement from management affirming the fairness of the system description and the suitability of the control design.
SOC 1 Type 2 Key Requirements:
-
Includes all Type 1 elements.
-
Testing Operating Effectiveness:
The auditor performs tests (inquiry, observation, inspection, re-performance) to gather evidence that controls operated effectively throughout the review period. -
Expanded Management’s Assertion:
Management also asserts that the controls operated effectively during the specified period.
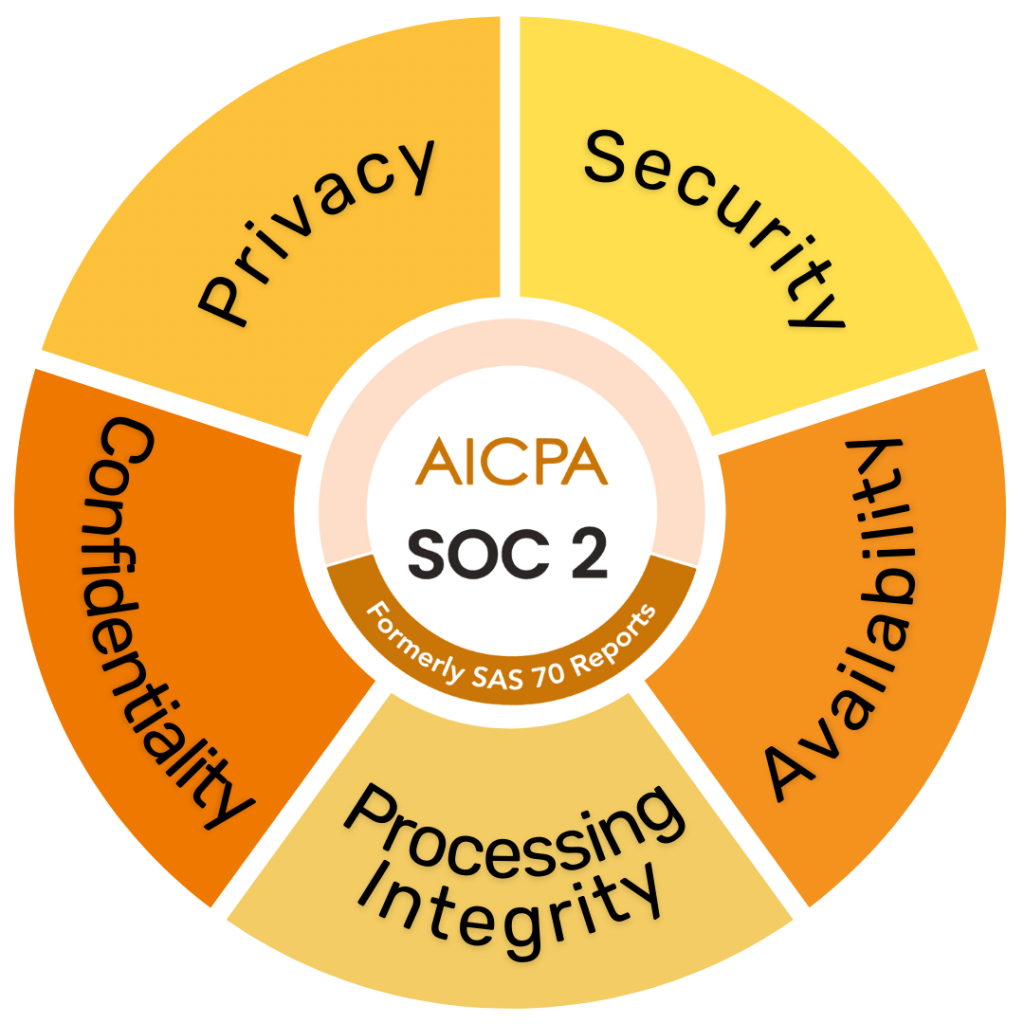
Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Unpacking SOC 2:
The Trust Services Criteria
SOC 2 reports are built around the AICPA’s Trust Services Criteria (TSC).
The Five Trust Services Criteria:
- a. Security (Common Criteria): This is mandatory for all SOC 2 reports. It addresses the protection of information and systems against unauthorised access, unauthorised disclosure, and damage.
- b. Availability: Concerns whether systems are available for operation and use as committed or agreed.
- c. Processing Integrity: Addresses whether system processing is complete, valid, accurate, timely, and authorised.
- d. Confidentiality: Focuses on protecting information designated as confidential from unauthorised disclosure.
- e. Privacy: Addresses the collection, use, retention, disclosure, and disposal of personal information in conformity with the organisation’s privacy notice and GAPP.
Service organisations select which of the optional TSCs (Availability, Processing Integrity, Confidentiality, Privacy) to include based on their service commitments and client needs.
SOC 2 Type 1 Key Requirements:
Management’s Description of the System:
Details the system components relevant to the selected TSCs.Suitability of Control Design:
An assessment that controls are suitably designed to meet the objectives of the selected TSCs as of the report date.Management’s Assertion:
A written statement affirming the fair presentation of the system description and the suitable design of controls for the selected TSCs.
SOC 2 Type 2 Key Requirements:
-
Includes all Type 1 elements.
-
Testing Operating Effectiveness:
The auditor tests if controls operated effectively throughout the review period to meet the objectives of the selected TSCs. Evidence collection involves inquiry, observation, inspection, and re-performance. -
Expanded Management’s Assertion:
Management also asserts the operating effectiveness of controls for the selected TSCs over the review period.
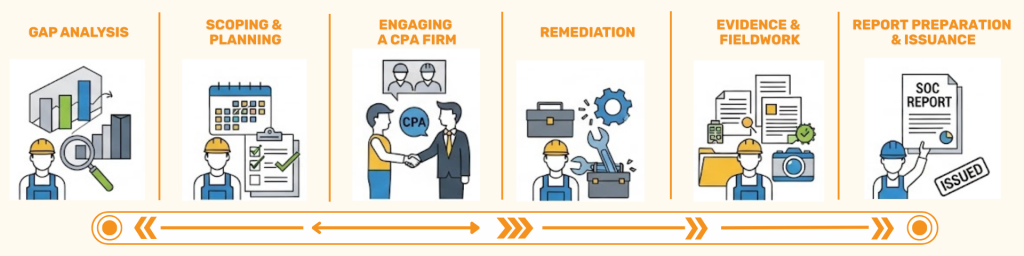
The SOC Audit Journey: Key Phases
Obtaining a SOC report is a structured process involving several phases and close collaboration with an independent CPA firm.
-
Readiness Assessment/Gap Analysis: Often the first step, this involves evaluating current controls against SOC requirements to identify and remediate gaps before the formal audit.
-
Scoping and Planning:
Defining the audit boundaries, selecting TSCs (for SOC 2), choosing the report type, and setting the audit timeframe. -
Engaging a CPA Firm:
Selecting a licensed, independent CPA firm with SOC expertise. -
Remediation:
Addressing any control deficiencies identified during the gap analysis. -
Evidence Collection & Fieldwork:
The auditors execute their procedures, reviewing documentation, interviewing personnel, and testing controls. -
Report Preparation & Issuance:
The CPA firm prepares the SOC report, including their opinion, management’s assertion, system description, and test results.
Preparing for Success:
Your Roadmap to SOC Compliance
Thorough preparation is crucial for a smooth audit and a favorable outcome. Consider these key steps:
- Understand Scope and Criteria:
Clearly define what’s in scope and which SOC report and criteria apply. - Assemble Your Team & Get Executive Buy-In:
Create a cross-functional team and ensure leadership support. - Conduct a Formal Risk Assessment:
Identify threats and vulnerabilities relevant to the audit scope. SSAE 18 emphasises this. - Document and Implement Controls:
Develop, document, and implement robust controls, policies, and procedures. - Manage Vendor Risk:
Implement a formal program for overseeing subservice organisations, as required by SSAE 18. - Prepare for Evidence Collection:
Establish processes to systematically gather and organise required evidence. - Communicate and Train:
Ensure all relevant staff understand their roles and responsibilities. - Monitor Continuously:
Implement processes for ongoing oversight of control effectiveness.
The Strategic Value of SOC Compliance
Achieving SOC compliance is more than just checking a box. It’s a testament to your organisation’s commitment to robust internal controls, operational integrity, and data protection. These reports are vital for building and maintaining trust with your clients and their auditors. In a competitive landscape, a SOC 1 or SOC 2 report can be a powerful differentiator, demonstrating your dedication to security and reliability. Ultimately, embracing the discipline of SOC compliance transforms a potential obligation into a strategic asset, reinforcing stakeholder confidence and paving the way for long-term business success.
With Sapience as your trusted partner in your SOC2 attestation journey, we will roll up our sleeves and walk the talk with you. Our hands-on partnership delivers direct support in the following key areas:

Readiness Assessment and Gap Analysis
One of Sapience Consulting’s most valuable contributions begins at the readiness phase. Many organisations, particularly SMEs and cloud-based service providers, struggle to interpret SOC 2 requirements in relation to their existing operations. Sapience can:
- Conduct a comprehensive gap analysis against the relevant Trust Services Criteria.
- Evaluate existing policies, procedures, systems, and documentation.
- Identify compliance gaps and provide actionable recommendations.
- Prioritise remediation efforts based on risk impact and audit criticality.
This preliminary phase ensures that organisations are not caught off guard during the formal attestation and that control design aligns with auditor expectations.

Customised Control Framework Design
Unlike other standards like ISO 27001, SOC 2 does not prescribe specific controls. This flexibility can be a double-edged sword for organisations unfamiliar with the Trust Services Criteria. Sapience bridges this gap by:
- Designing tailored internal controls aligned with the organisation’s business model and chosen TSCs.
- Mapping SOC 2 requirements to industry best practices and frameworks such as NIST CSF, ISO 27001, or COBIT.
Helping define a risk-based scope of controls that avoids overengineering.
This step is especially useful for cloud-native businesses, SaaS providers, fintech startups, and regulated industries in Singapore where compliance with PDPA and MAS TRM guidelines often overlap with SOC 2 expectations.

Policy Development and Documentation
Policy and documentation are cornerstones of a successful SOC 2 audit.
Sapience Consulting brings value by:
- Drafting or enhancing critical policies like access control, data retention, incident response, and vendor risk management.
- Creating documentation such as a System Description, which is mandatory for SOC 2 reports.
- Ensuring documentation reflects actual practices, minimising audit exceptions.
For Singapore-based companies, Sapience can contextualize documentation to address local regulations such as the Personal Data Protection Act (PDPA)
and sector-specific codes of practice.

Implementation Support and Training
The most well-crafted policies fail without effective implementation. Sapience doesn’t stop at advisory—we offer hands-on implementation support, which may include:
- Deploying monitoring tools, ticketing systems, or compliance automation platforms.
- Assisting with the setup of evidence collection workflows to demonstrate operational effectiveness.
-
Conducting training sessions for employees on compliance practices, security awareness, and control responsibilities.

Vendor Management Program Setup
SOC 2 under SSAE 18 requires service organisations to manage third-party risks. Sapience helps by:
- Developing vendor risk management frameworks.
- Establishing procedures for due diligence, onboarding, and continuous monitoring of vendors and subservice providers.
-
Documenting vendor SLAs and contractual obligations in alignment with SOC 2 expectations.
This is particularly relevant in Singapore’s ecosystem where data residency and cross-border data transfers are governed under PDPA and IMDA guidelines.

Audit Facilitation and Liaison with CPA Firm
Once the organisation is ready for formal attestation, Sapience acts as a liaison between the business and the independent CPA firm conducting the audit. We can :
- Support the selection of an auditor with the right experience and fit.
- Coordinate audit timelines, evidence gathering, and contol walkthroughs.
- Prepare the organisation for management interviews and walkthroughs.
Clarify auditor queries and ensure accurate interpretation of control narratives.
This ensures a smoother, faster audit process with fewer disruptions and misunderstandings.
Continuous Monitoring and Improvement
SOC 2 Type 2 audits assess control effectiveness over 6-12 months.
Sapience supports ongoing compliance by :
- Establishing metrics and dashboards for monitoring control health.
- Performing mock audits or internal checks mid-cycle.
-
Updating policies and evidence repositories as environment evolve (e.g. infrastructure changes, new regulatory mandates).
They can also advise on expanding to SOC2+ frameworks (e.g. HIPAA, GDPR) using the same control foundation, providing long-term strategic value.
In Singapore’s dynamic digital landscape, securing your data is not just a requirement—it’s a responsibility. We at Sapience have seen the devastating impact of security breaches, and we believe that your SOC 2 attestation should be a testament to your integrity and dedication. Partnering with us is a declaration of strength, a strategic move that empowers your organisation to confront these challenges head-on. With our proven expertise and unwavering support, we stand with you, arming you with the tools and knowledge needed to transform your SOC 2 journey into a shield—a symbol of your resilience and dominance in a security-conscious market.
As a trusted leader in professional development, Sapience empowers you to invest in your future.
Don’t wait – Explore our available funding and leverage our expertise to upskill without financial strain.










